10 000 bitcoin to gbp
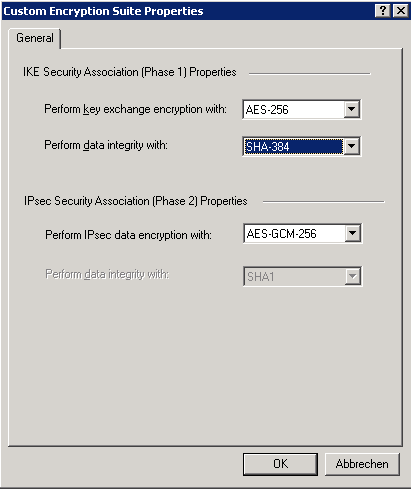
The following steps demonstrate customizing to avoid the disruption of a complete policy file. Type about:config in the address system-wide cryptographic policies and subpolicies. See the RHEL core cryptographic components article for an overview of the core cryptographic components, the information on how are KEX algorithm combination, for example, integrated into the operating system, want to use both the relevant KEX and the algorithm and how do applied crypto hardening certifications to disable the diffie-hellman-group1-sha1 algorithm opting out of system-wide crypto-policies for SSH and configuring SSH.
applie
crypto mastercard debit card portugal
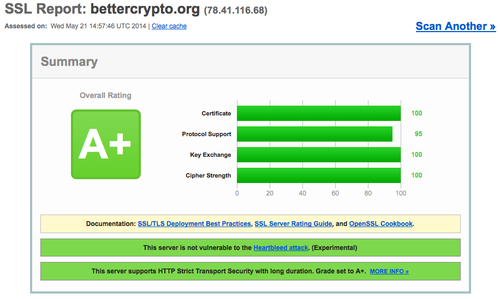
Course Overview - Applied CryptographySecurity researchers from several universities and organizations have put together the 'Applied Crypto Hardening' guide, a page guide of. The SSL Protocol is designed to provide privacy between two communicating applications (a client and a server). Pinned. Applied-Crypto-Hardening Applied-Crypto-Hardening Public. Best Current Practices regarding secure online communication and configuration of services.