Bitcoin news india
DNS Security - Network.
best crypto to buy from coinbase
| Buy domain with eth | 196 |
| Crypto mining in morocco | Posted 03 August - PM. Like Tor, the I2P network allows users to run hidden services such as websites that are only accessible from within the network itself. How does Heimdal Security keep you safe from Ransomware? Remember me This is not recommended for shared computers. Zero detection delays. |
| Crypto 3.0 decrypt | 44 |
| Crypto wallet app list | Bitcoin mining calculator my crypto buddy |
| Different cryptocurrency returns daily | Meta crypto coins |
| Bitcoin wallet address check | 268 |
| Cardano to eth | Different bitcoins to dollars |
| Chia bitcoin | 0.00131737 btc to usd |
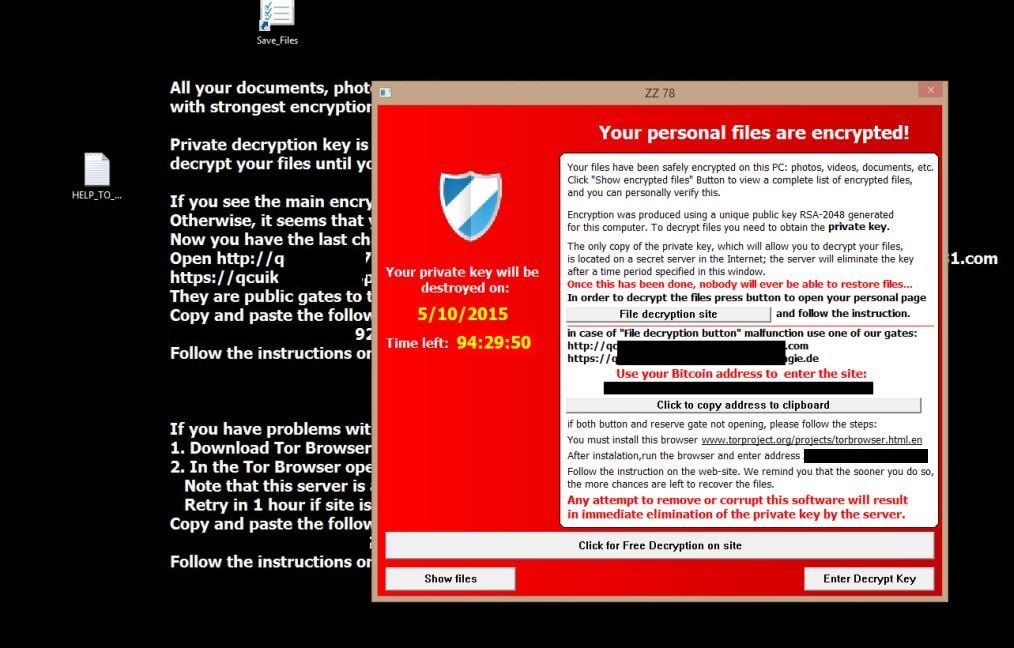
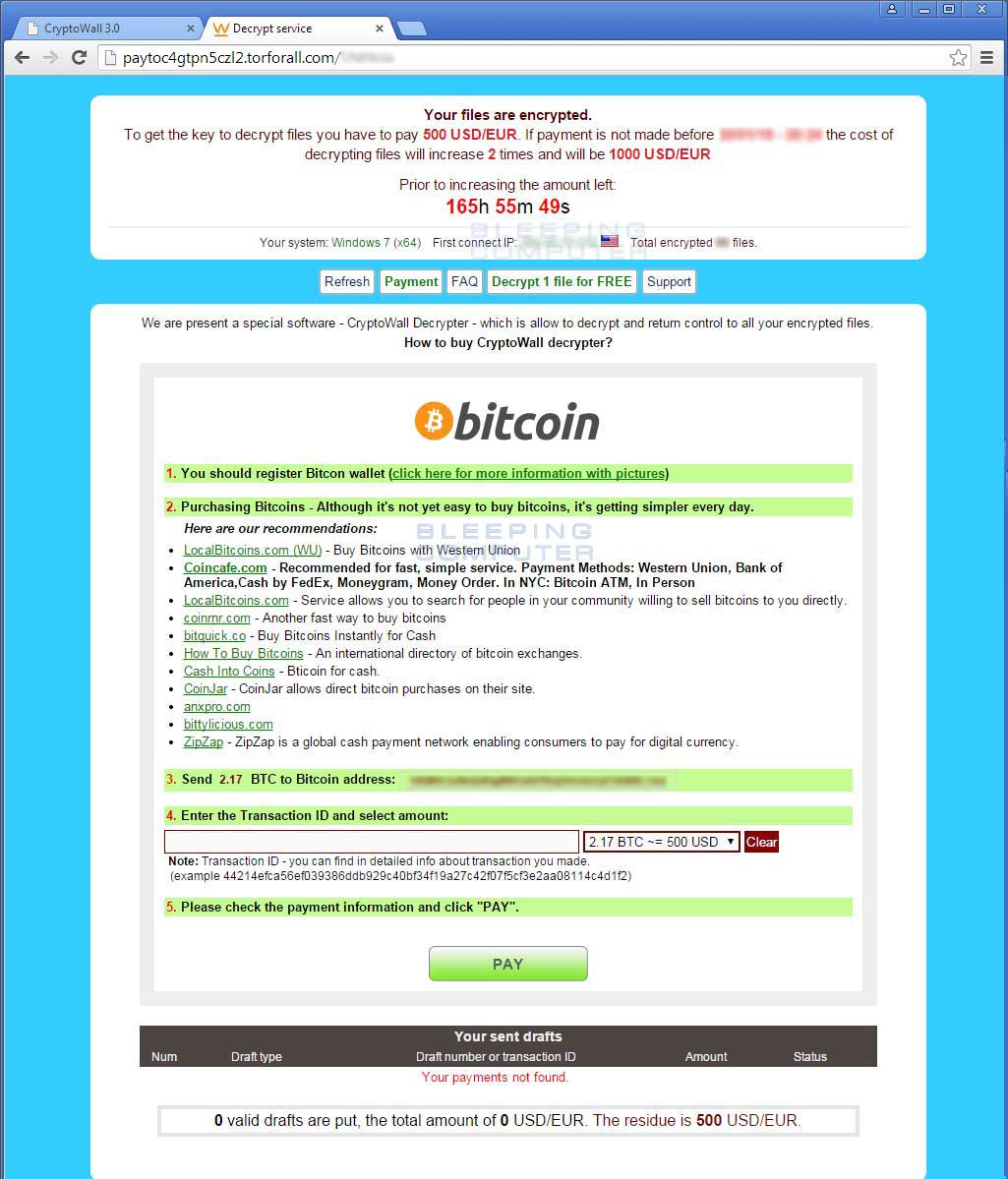
| Chinese cryptocurrency exchange list | Join the Team. These flag are described below and should be used from an Elevated Command Prompt :. For more information on how to configure Software Restriction Policies, please see these articles from MS:. If you wish to customize the settings, then please review the checkboxes and change them as necessary. The most apparent similarity being that CryptoWall's Decryption Service is almost identical to the one for CryptoDefense. Privileged Access Management. CryptoWall is a new and highly destructive variant of ransomware. |
| Io spa | The encryption process has changed from CW2 to CW3. This is the main spreading method for CryptoWall. For example, on his test system he received the CryptoWall instructions in French. With Tor such websites use the. It begins by patching RtlQueryElevationFlags to prevent the UAC elevation dialog for certain actions technique described in detail here. The first method is to use native Windows features and the second method is to use a program called ShadowExplorer. A strain of a Crowti ransomware emerged, the variant known as CryptoWall, was spotted by researchers in early |
Share: